What is SQL injection? How can it affect your web application?
In the Cyber Security world especially Web Application Security is considered one attack is always in the talk that is SQL injection. The Open Web Application Security Project also called as OWASP releases the OWASP Top 10 2017. A list of top vulnerabilities in Web applications. In this document SQL Injection ranks as the number one threat to web application security.
This blog will give you insights of complex SQL injection in simplest words
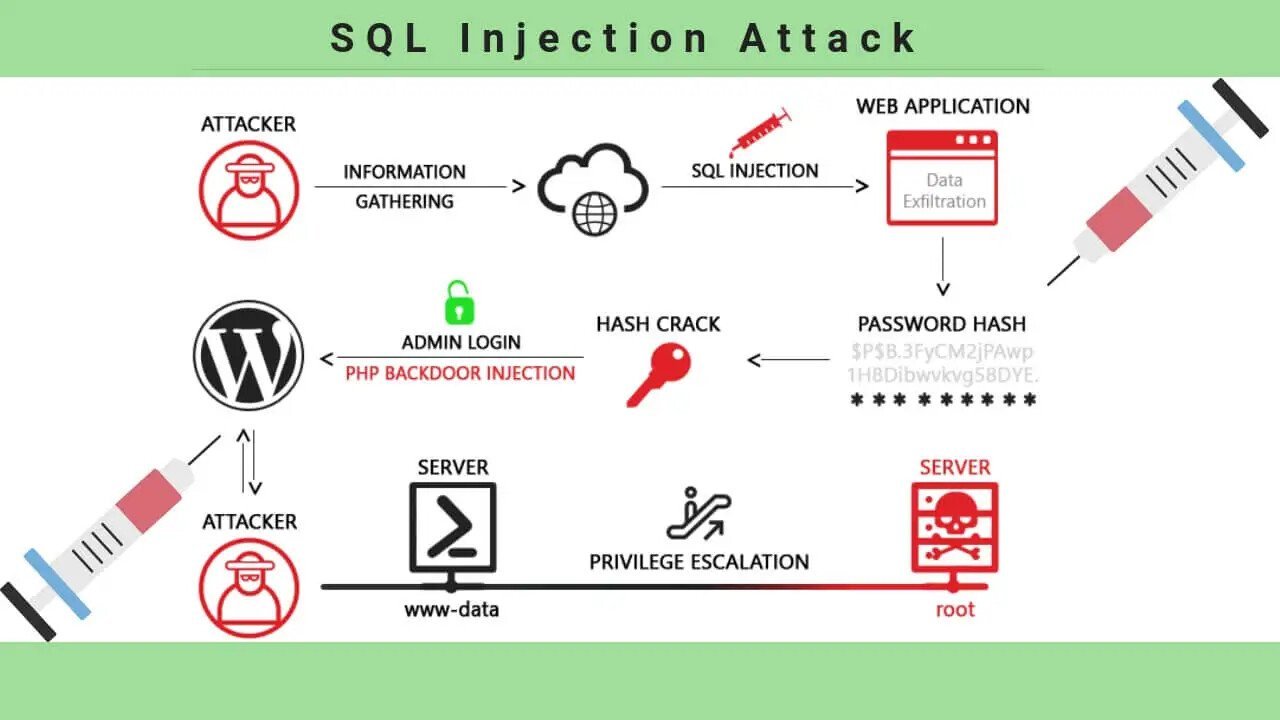
What is SQL Injection ?
SQL stands for Structured Query Language it is a query language that was designed to manage data stored in relational databases. It is used to access, modify, and delete data. Most of the web applications and websites store all the data in SQL database. Hence, a successful SQL Injection attack can have very serious consequences. SQL lets the user select and extract data from the database. An SQL Injection could allow the attacker to gain complete access to a database server.
SQL also allows alter data in a database and adds new data. For e.g. There is a financial application, in that an attacker could use SQL Injection to manipulate balances, alter transactions, or transfer money to other accounts.
In simplest words Sql injection is nothing but a technique which can be used to take advantage of non-validated inputs to insert SQL commands through a web application for execution by a backend database. Basically it is trying to gain unauthorized access to a database or to retrieve information directly from the database.
SQL injection is a web security vulnerability that allows an attacker to modify the SQL queries made to the database. This can be used to get some sensitive information, like structure of database, tables, columns, and data.

How does it work ?
Consider the following basic example.
Suppose an application uses the following query to fetch someone’s login details:
SELECT USERNAME,PASSWORD from USERS where USERNAME=” AND PASSWORD=”;
Here, username and password is the input provided by the user. Suppose an attacker gives the input as ‘ OR ‘1’=’1 in both fields. Therefore, the SQL query will look like:
SELECT USERNAME,PASSWORD from USERS where USERNAME=” OR ‘1’=’1′ AND PASSWORD=” OR ‘1’=’1′;

Here when the USERNAME field’s value is being checked it will return TRUE because the OR operator will return the TRUE value from the comparison of ‘1’=’1′. Same will happen in case of the PASSWORD field. By combining both results the final result of AND operator will be returned as TRUE to the Login request query which will result in bypassing the Login mechanism. This example explains the most basic type of SQL injection.
Impact
SQL Injection makes it possible to execute malicious SQL statements. Such statements can control a database server behind a web application. Attackers can use SQL Injection to bypass application security controls. It can go around authorization and authentication of a web page or web application and gain the content of the entire SQL database. The SQL Injection can be used to add, modify, and delete records in the database.
Depending on application used and the way it processes user supplied data, SQL injection can be used to implement the attacks mentioned below :-
1) Authentication bypass – Using this attack , an attacker logs into the application without providing a valid user name and password and gains administrative privileges.
2) Information disclosure – Using this attack, an attacker obations sensitive information that is stored in the database
3) Compromised data integrity – An attacker uses this attack to deface a web page, insert malicious content into web pages, or alter the consents of a database.
4) Remote Code Execution – It assists an attacker to compromise the host OS
How to Prevent ?

SQL Injection flaw in web applications and not a database or web server issue. The main factor that leads to SQL injection is :
⦁ Improper error handling.
Improper error handling can be an easy entry point for an attacker to try the SQL injection. Any error in the back end of the application should be handled there only it should not be visible to the front end. If it is then it is improper error handling. It discloses the back end information thus can be reason for the back end information disclosure through SQL injection.
⦁ Poor Input sanitization.
Every web application where any kind of input is accepted such as login form , sign up form, etc. the input should be sanitized. Proper input validations should be applied to the input so that it should verify the input values going to the database through web applications. If there are no input sanitization provided then any malicious input can be passed through the web application causing the possible damage like information disclosure through SQL injection.
⦁ Passing a query directly with the user’s input.
User inputs are the information which will be used in processing of query. If the query and the inputs are not isolated then there will be dependencies between them. Hence in case of malicious inputs or malicious requests there will be ease of execution. Like in SQL injection an malicious request is passed to the back end in order to extract the information.
To have practical and detailed information about these factors, you can look for ethical hacking course where they guide you theoretically and practically.
Hence the following are ways to prevent SQL Injection attacks :
1) Input validation
2) Parameterized queries including prepared statements.
3) Application code should never use the input directly.
4) The developer must sanitize all inputs.
5) Potential malicious code elements should be removed such as single quotes.
6) Turn off the visibility of database errors on User interface as database errors can be used with SQL Injection to gain information about your database.
Plus if you want to study more about this SQL injection and want to protect your own web application from this attack, you can join any ethical hacking course in pune, where you should find one of the top mentor will provide you detailed information and prevention measures for this attack.